Penetration Distributions
Publish date: Aug 10, 2019
Last updated: Apr 22, 2020
Last updated: Apr 22, 2020
IMAGE GALLERY (9)
Bastion Host ACL - access control list
- Doing something that it is not supposed to do. Act of hacking.
- Ethical when companies ask you to do so. Is in the constraints of law
- Perople will pay to detect vurnabilities and even pay to fix it.
- Anonymity is the key, prefer Linux, most hacking tools are native to windows.
- People like White(within law)/ Grey/ Black(financial gail)
- extract information from servers
- steal credit card information
- take services down
- steal Authentication information
- Footprinting
- IP of server
- Which ports are open and guessing which services are running
- Information gathering (either digitally or physically)
- DoS - denial of service, make more than 10,000 requests per sec and whwn apachey can’t process them
- no firewall bypass required
DDOSRemote administration tools,FUDFully undectitable, not detected by antivirusRATRemote Administration Tools, malwares to make new slavesRootkitable to hide running processes from task manager. System call to kernel, intercepts requests and manupulates it.Fishingkind of bait to promote certain actions. DNS servers gets chaines from your router and you get served by other servers, might look exactly the same and your credentials are stolen- Always check for
HTTPS
- Always check for
- SQL Injections, some popular web frameworks are vurnable to this attacks
- VPN
- SOCKS5 Proxys, Procy chains, limited by bandwidths
TORonion routing, free to use, anonymous to a very large extent, access Dark Web- VPS - Virtual Private Server, only users from certain host/ n/w could access a service
Keyloggerssteal information and then send email, can send existing info as well, like screenshots, turn on camera etc- Firewall
Reverse Shellsinfect device, which connects back to you. Sometime need to break into routers first. Fishing attacking are possible
describe the reasons an attacker would have to attack the application. You will be putting their shoes on after all. for example, is the application storing sensitive data that could be the target of a hacker, and so on.
Pen Test Reports
- https://www.offensive-security.com/reports/sample-penetration-testing-report.pdf
- https://www.radicallyopensecurity.com/report_otf_fdroid.pdf
- https://github.com/juliocesarfort/public-pentesting-reports
- https://www.shiftleft.io/images/extended-shiftleft-web-201806-20180728-0007.pdf
- https://pulsarweb.de/Pentest_Report.pdf
Pen test management tools
- Reconnaissance
- Social Engineering
- Scanning
- Port Scanning
- Legal
- Nmap is to always secure written authorization from the target network representatives before initiating any scanning
- Include a written permission and Statement of Work
- Dates and times for scanning
- IP ranges to be scanned
- Names of systems and networks to be scanned
- Scanning tools to be used
- People conducting the scans
- If a remote scan is planned, include the IP address of the scanning tool
- Sandbox scans
- Gaining Access
- Maintaining Access
- Covering Tracks
- tor network, onion routing
- i2p network
- Invisible internet project
- Parrot OS
debianstandard based, 2013- Can run on RaspberryPi
- Extra tools
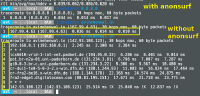
WifiPhisheranonsurf
- Kali Linux / BAcktracking
debianstandard based
- BlackArch Linux
- Was unable to install
hugofrom snap usermodcommand not installed, to modify group setting and I could not find where to install it- Unable to run docker, installed as
docker.iopackage
- Most FTSI The Financial Times Stock Exchange 100 Index are affected by data/information leaks
- All fortune 100 companies are equally affected no matter how big you are
- Demo - script that tries to login to 20 different websites
- Password reuse style attacks
- How to mitigate
- Use Password Managers
- https://www.lastpass.com/
- https://www.dashlane.com/
- Enable 2-factor Authentication
- Dummy Email ID for sites you do not trust
- Burner accounts
- Way to delivery Virus models
- Way to find ways runs codes on computers
- emails, videos
- send and email with attachment, they click and open it. because thats what you do with attachments
- executables on video players, files
- you can block an many delivery vectors as you can, but its the payload that counts
- IT infrastructure is strong but
Telecom Infrais still weak - tools to search github for username/pass
- these days we have
- Ransomeware As A Service
- DDoS for hire
- IoT based Botnets
- Commodity Cybercrime tools
- Industrial Control System - dont connect them to internet - Airgap
- Pen Testing is QA shop
- Finding bugs to sell
- Bug database
- internal insights on how fequently a bug appears
- and how long does it takes companies to solve it
- ML to generate passwords
- On sight in datacentre time - Util time
- Password encryption standards - definately not
base16its 2019 Grammeris important -Fuzzying- fucking with input- If you know the grammer, you can emit/mutate input language
- https://github.com/MozillaSecurity/dharma
- https://zerodium.com/
- States Matters in softwares
- they have protocols to follow
- logedin state, logged out state, admin role etc
- Stateful Fuzzying
- https://en.wikipedia.org/wiki/Symbolic_execution
- analyzing a program to determine what inputs cause each part of a program to execute
- You define the goal state and let execution take care of rest
- like find a solution to a puzzle
- https://en.wikipedia.org/wiki/Program_synthesis
- let magic and sciencce do the hard work.
- Monte carlo tree search *
- Stop
Cuserustitsmemory-safe,type-safe, can do stuff which java .net cannot do - Embrace Automation
- SHODAN (Sentient Hyper-Optimized Data Access Network)
- Heartbleed damage report
We need to up our game
- LulzSec1
- https://en.wikipedia.org/wiki/WannaCry_ransomware_attack
- MS-17-010
- Hybrid Encryption scheme
- Files encrypted by
AESand that key is protected by public key cryptography
- https://www.makeuseof.com/tag/5-of-the-worlds-most-famous-hackers-what-happened-to-them/ 4.